Cyber threats and actors know no borders. One single entity victim of a cyber attack can trigger a domino chain reaction, creating spill-over effects across the Union. The European Member States, with their National Coordination Centres are the leading Cybersecurity authorities, acting as a guide to best security practices for public and private sectors. However, different certifications, guidelines, practices and penalties are applied per state, this heterogeneity of measures creates gaps and could result in certain Member States becoming more vulnerable to cyber threats. To prevent this, a unified criterion has been established, for a Joint Cybersecurity EU, creating the new directive NIS2.
New directive : NIS2
To harmonise compliance regulations and have a baseline for cybersecurity risk-management measures, the European Commission has updated the NIS directive (from 2016), emphasising on a common criterion for all Member States and extending the scope of concerned entities. So, what’s new?
Scope’s extension
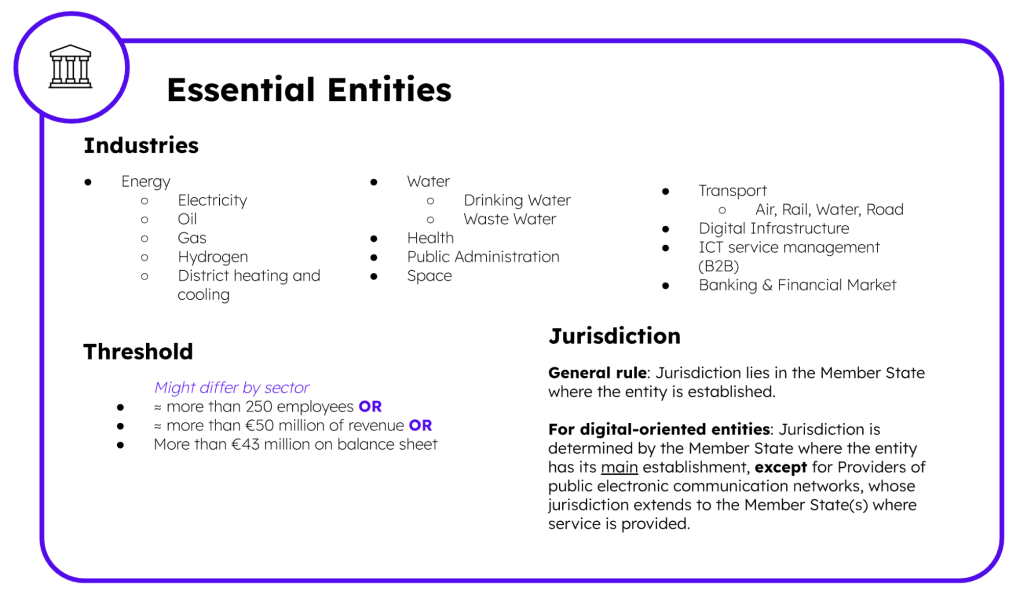
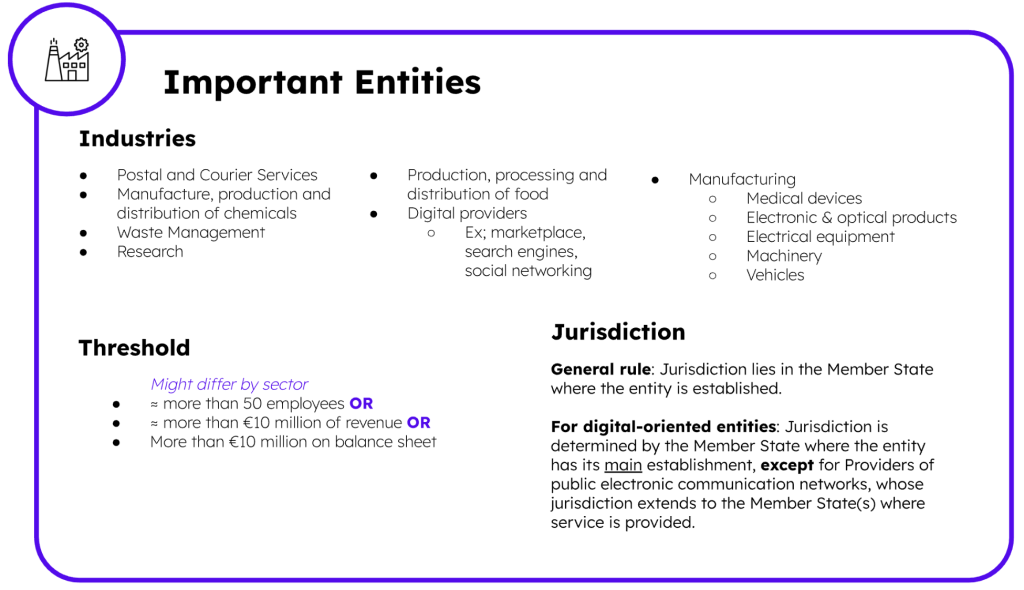
NIS2 introduces two types of entities: important and essential entities. This distinction is made by the type of industry and services provided by the company, as well as their possible impact on the economy if a security incident were to happen. By including more industries into this Joint Cybersecurity Effort, NIS2 is accentuating the need to prevent supply chain attacks, impacting the whole Union.
Key entities identified by each Member State must adhere to the new Directive by October 2024, which introduces a comprehensive framework of cybersecurity risk-management measures and reporting obligations:
Reporting
The reporting process should support an automatic and direct reporting mechanism for immediate share of information with relevant authorities. Incident Notification templates and supervisory processes should be harmonised for all Member States to minimise administrative burden.
Obligations
NIS2 strengthens the obligation to follow its regulation; now, C-levels and natural persons representing entities will be directly held accountable and liable for failure to comply and report.
If failure to comply, administrative fines for:
> Essential Entities : a maximum of at least EUR 10 000 000 or of a maximum of at least 2 % of the total worldwide annual turnover in the preceding financial year of the undertaking to which the essential entity belongs, whichever is higher.
> Important Entities : a maximum of at least EUR 7 000 000 or of a maximum of at least 1,4 % of the total worldwide annual turnover in the preceding financial year of the undertaking to which the important entity belongs, whichever is higher.
Risk Management
A great emphasis is placed around cybersecurity risk management as well as resilience. The second directive (EU) 2022/2557 highlights two measures for critical entities to comply with NIS2.
Risk Assessment
Critical entities will have to thoroughly evaluate the risk associated with their business operating in cyberspace, as well as the physical and environmental security of the network. Every Technical Authority should be able to report that those entities (both important & essentials) have a risk assessment carried out. This assessment should include measures to identify any risks of incidents, to prevent, detect, respond to and recover from incidents and to mitigate their impact. One novelty, is the human factor being stressed out in the Directive : critical entities will have to follow a strict background check and strengthen their access policies to reduce the risk of the human factor in cybersecurity related incidents.
Resilience Plan
Security incidents are unavoidable, therefore, NIS2 lays down the principle of resilience. This is translated into a Resilience Plan where the entity needs to describe all measures taken that sufficiently achieves the aims of effectiveness and accountability, in regards to all the risks previously identified. NIS2’s aim in that regard is to harmonise all the rules for European Countries, to ensure the provision of important and essential services and therefore enhance the resilience of the latter, especially to avoid any disruption of the overall supply chain of ICT services. Reporting obligations from affected entities will be driving the “lessons learned” to improve the cyber resilience of entities and sectors.
How to achieve this?
“Responsibility for ensuring the security of the network and information system lies, to a great extent, with essential and important entities”.
NIS2 highlights operational and organisational measures to manage the risk posed to the security of network and information systems, however, the implementation of risk-management measures would still be on the entity’s shoulders. Technical Authorities and frameworks guide entities on operational and technical implementation of those directives. Below several measures are enforced by the Directive;
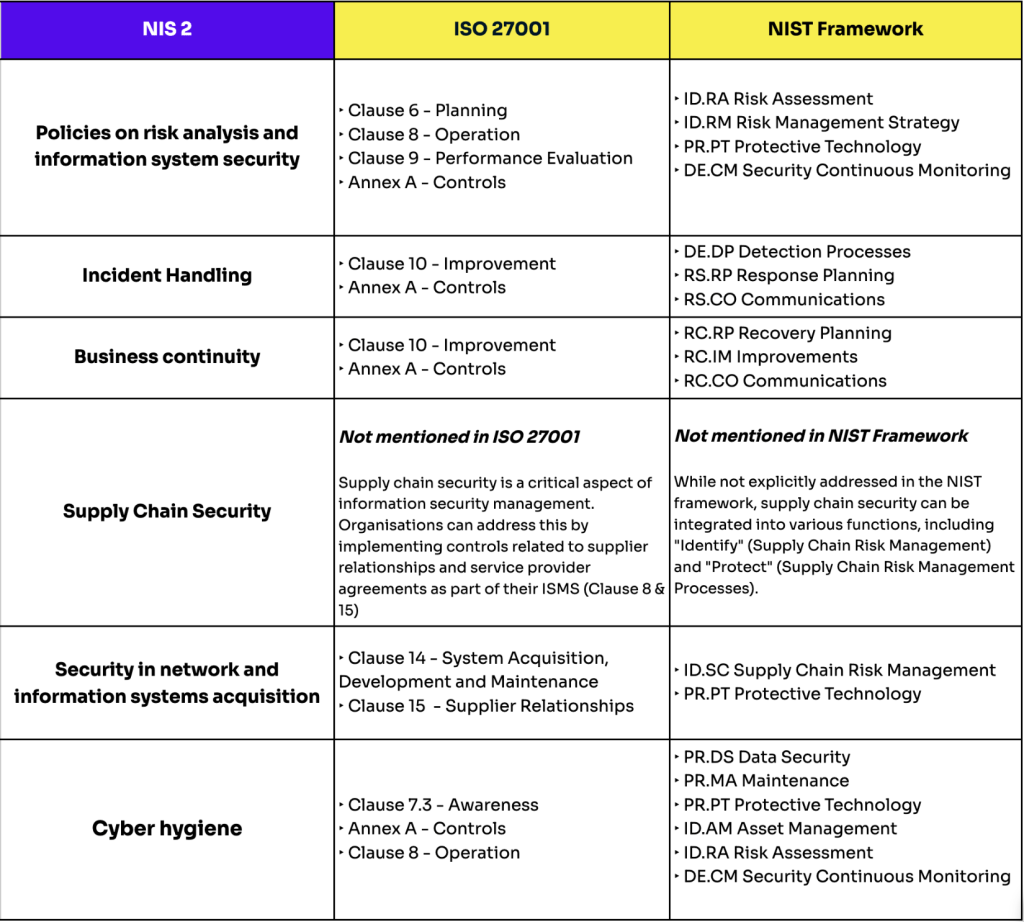
Policies on risk analysis and information system security
Tying to the new NIS2’s obligations, risk assessment and management will be the cornerstone of every entity willing to comply with the directive. NIS2 refers to ISO/IEC 27000 series in line with this measure.
While ISO/IEC 27001 provides the requirements for risk assessment, the best practices and measures to be implemented are laid out in ISO/IEC 27002 & ISO/IEC 27005. Additionally, the French Cybersecurity Agency, ANSSI, is providing a comprehensive set of guides around risk management, with EBIOS, breaking down the methodology to evaluate & managing risk.
Incident Handling
Incident Management is a set of procedures & steps to identify, contain, respond and resolve an incident, and ultimately, reduce the impact of similar incidents in the future. ISO 27001 helps the entities setting risk assessment and management (as set in policies on risk analysis) procedures to tackle the preparation phase of any Incident Response Plan. NIST Framework lays the technical controls for an efficient incident response cycle, in 4 phases:
- Preparation
- Detection and Analysis
- Containment, eradication & recovery
- Post-incident activity
(Check out this full guide on Incident Management)
Business Continuity
Attacks are inevitable, and eventually, will happen. It is crucial to be prepared in order to recover from them. Effective recovery not only safeguards these operations but also protects the security of employees and citizens. This principle is extensively covered in ISO 27001, and it is a key requirement entities should pay attention to.
Supply Chain Security
This is the novelty of NIS. The European Union Agency for Cybersecurity (ENISA) has declared that Supply chain Attacks are one of the most concerning threats for Europe in 2024. To respond to that, NIS2 emphasises on a homogeneous directive, as our economic and IT spaces are deeply interconnected, and “if one falls, we all fall”. As such, entities should incorporate reviewing logs at the contract renewal point for vendors to determine whether there is a systemic problem, and review cyber security practice and maturity of each of their suppliers.
Security in network and information systems acquisition
“Security by design”, an approach incorporating security measures as a foundational part of software development, throughout the entire lifecycle. Some key principles includes minimising the attack surface by limiting any potential entry point for malicious actors, principle of least privilege, giving only to an employee the key they need. Another dimension of this measure, related to Supply Chain security, is to ensure
Cyber Hygiene
On this bullet point, I can only refer you to the “Guideline for a Healthy Information System” from the French Cybersecurity Center. This measure from NIS2 really means basic security measures that any entities could implement, from security training to having an asset inventory. The document takes you through each measure, and give you the minimum effort to take.
Want to see how each measure aligns with different parts of compliance frameworks?

Leave a comment